Weak Links in Authentication Chains: A Large-scale Analysis of Email Sender Spoofing Attacks
摘要
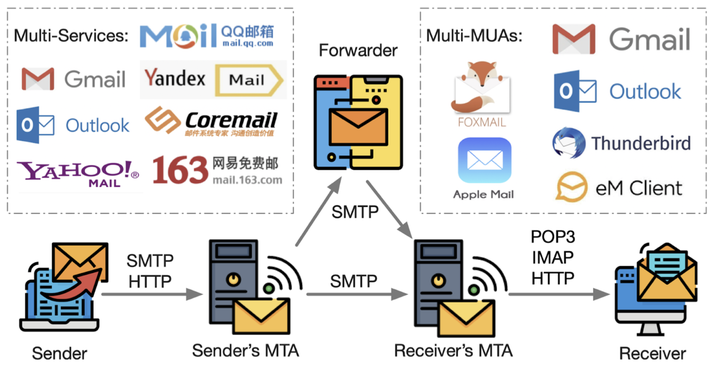
As a fundamental communicative service, email is playing an important role in both individual and corporate communications, which also makes it one of the most frequently attack vectors. An email’s authenticity is based on an authentication chain involving multiple protocols, roles and services, the inconsistency among which creates security threats. Thus, it depends on the weakest link of the chain, as any failed part can break the whole chain-based defense. This paper systematically analyzes the transmission of an email and identifies a series of new attacks capable of bypassing SPF, DKIM, DMARC and user-interface protections. In particular, by conducting a cocktail joint attack, more realistic emails can be forged to penetrate the celebrated email services, such as Gmail and Outlook. We conduct a largescale experiment on 30 popular email services and 23 email clients, and find that all of them are vulnerable to certain types of new attacks. We have duly reported the identified vulnerabilities to the related email service providers, and received positive responses from 11 of them, including Gmail, Yahoo, iCloud and Alibaba. Furthermore, we propose key mitigating measures to defend against the new attacks. Therefore, this work is of great value for identifying email spoofing attacks and improving the email ecosystem’s overall security.
眼见不一定为实:对电子邮件伪造攻击的大规模分析
简介
作为互联网上部署、应用最广泛的基础通信服务,电子邮件服务在企业和个人通信中都扮演着举足轻重的角色。基于电子邮件伪造攻击的钓鱼欺诈、勒索软件和病毒木马已成为当前威胁互联网安全最严重的攻击,并给相关企业和个人造成了重大财产损失。虽然不断有新的安全机制被引入来保护电子邮件的安全性(如发件人策略框架(SPF)、域名密钥识别标准(DKIM)和基于域的消息验证、报告和一致性(DMARC)等安全扩展协议),但是基于电子邮件伪造的攻击依然屡禁不止。 为了找到目前邮件伪造攻击频发的原因,并从根源上提高电子邮件系统的安全性,该研究基于电子邮件传输过程对电子邮件伪造问题进行了系统性的实证研究。该研究共发现14种可绕过SPF、DKIM、DMARC以及UI保护机制的电子邮件伪造攻击方法。为了测量这些攻击在现实中的实际影响,该研究针对全球30家主流邮件和23个邮件客户端进行大规模实验与分析。实验结果表明这些主流邮件服务和客户端均受到了不同程度的影响,其中甚至包括Gmail、Outlook等知名邮件服务商。
这一研究成果发表于网络安全领域顶级会议USENIX Security 2021上。
- 论文题目:Weak Links in Authentication Chains: A Large-scale Analysis of Email Sender Spoofing Attacks(本文已被USENIX Security 2021录用)
- 论文作者:沈凯文, 王楚涵(并列一作), 郭明磊, 郑晓峰, 陆超逸, 刘保君, 赵宇轩, 郝双, 段海新, 潘庆丰, 杨珉
- 作者单位:清华大学,奇安信技术研究院,德州大学,复旦大学,Coremail论客技术有限公司
- 论文下载:https://www.usenix.org/conference/usenixsecurity21/presentation/shen-kaiwen